Ransomware is a plague that most business executives think will not happen to them.
Often - even when hit once or more, they feel people have "learned their lesson," and won't click again.
Reality shows this is not the case.
First of all, there is natural turnover of workers in companies - new employees may or may not know what not to click on. Also, ransomware attackers are getting better. There is a treasure-trove of personal information on virtually all workers on the dark web. It is very ease to personalize messages which appeal to anyone in the hopes of getting them to click.
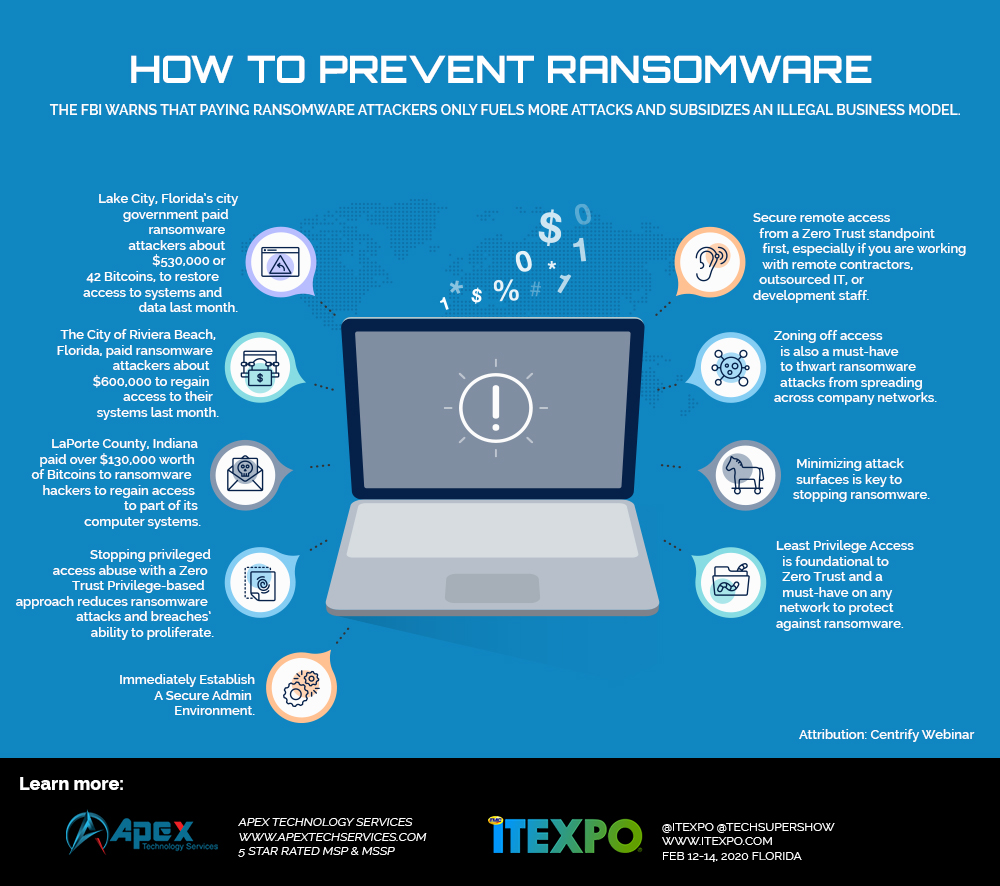
The recent ransomware attacks on Lake City, Florida, Riviera Beach, Florida, LaPorte County, Indiana, the City of Baltimore, Maryland, and a diverse base of enterprises including Eurofins Scientific, COSCO, Norsk Hydro, the UK Police Federation, and Aebi Schmidt reflect higher ransoms are being demanded than in the past to release high-value systems. There’s been a 44% decline in the number of organizations affected by ransomware in the past two years, yet an 89% increase in ransom demands over the last 12 months according to the Q1, 2019 Ransomware Marketplace Report published by Coveware. The Wall Street Journal’s article “How Ransomware Attacks Are Forcing Big Payments From Cities, Counties” provides an excellent overview of how Ryuk, a ransomware variant, works and is being used to hold unprepared municipalities’ IT networks for ransom.
The above infographic based on a Centrify webinar gives solid ways to protect your organization.
What else should you know?
We have put together cybersecurity essentials – a simple list which will help most organizations become far more secure.
Please go to a phishing simulation vendor now and sign up for one of their offerings. Phishing Box, KnowBe4 and Phish360 are all great.
We also recommend you get a free evaluation of your cybersecurity risk from an MSP/MSSP immediately.



