Cybersecurity
Cybersecurity Overview
Apex Technology Services has the cybersecurity expertise to help your business in a world filled with attackers looking to shut down your business, hold it for ransom or steal your valuable business data. We have spent years customizing our security offerings to help your company meet compliance obligations as well as meet your fiduciary responsibility to corporate stakeholders. Our security offerings contain layers of redundancy to help ensure business continuity.
In the past years, the White House, Anthem, Staples, Home Depot, IRS, Target and many other high-profile companies have been attacked. Moreover, companies of all sizes are forced to pay ransoms totaling more than billions of dollars per year
per year thanks to a potential single CryptoLocker ransomware click by an unsuspecting employee.
Once infected by such an attack, an entire network of data can quickly become password protected by the malicious user who holds your data hostage until adequate payment is received. Moreover, it is not uncommon for a ransomware target to be hit repeatedly over the course of time.
Even worse, there is no way to determine who is receiving the payment. It could be a rogue nation or terrorist group. There is also no way to be sure data will be unlocked once payment is made. Even if it is, it could be infected with an advanced persistent threat (APT) which activates at a later date.
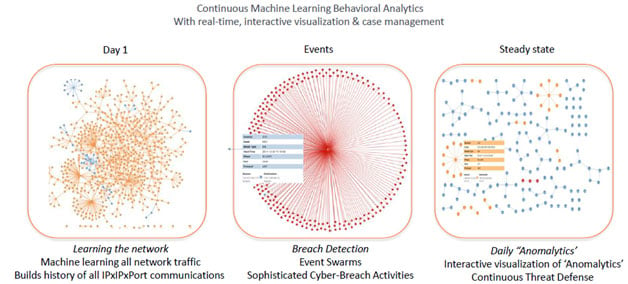
Anomaly Detection/Analytics
Apex Technology Services will pinpoint vulnerabilities in your infrastructure, process flow and internal security to ensure you are securing your data behind layers of security.
Anomaly detection and behavioral analytics are used to fight Advanced Persistent Threats (APTs) used in cyberespionage from nation-states, hackers, employees, competitors, and others with malicious intent. Current security solutions are not enough. Expert hackers know how to hide their activities within the everyday noise of networks. They are becoming more sophisticated and have dramatically changed the threat landscape.
To be more proactive against cyberattacks, organizations must detect high-risk activities during the reconnaissance phase. Waiting for external communication through the perimeter is too late and can have disastrous consequences. Detecting and stopping attackers inside the network, requires gathering network data and applying advanced behavioral analytics to recognize normal patterns vs anomalous patterns likely to be the activities of an attacker.
Apex Analytics Security Platform
- Multi-dimensional, multi-model, streaming algorithms
- Not based on any rules, signatures, patterns or heuristics
- High computation efficiency, real-time threat/risk detection
- Unsupervised machine-learning, minimal configuration settings
Continuous Security Threat Assessment
- Segmentation: Limit & monitor the attack surface
- Security Hygiene: Continuous employee-risk analysis
- Advanced Threats: Continuous anomaly detection
Cyber Security & Industrial Internet of Things
- Scalable to very large networks of IP devices
- Not based on rules, signatures or heuristics
- Unsupervised machine learning based on non-linear behavioral clustering using self-organizing maps
Implementation
- Installed in a day, on passive network tap/span port
- Typically off core switch or network segment
- Small footprint, Virtual VM, platform independent
- Software as a Service model
Training
Employees are one of the major sources of cybersecurity risk for firms. FINRA found that many of the cybersecurity attacks that firms identified were successful precisely because employees made mistakes, such as inadvertently downloading malware or responding to a phishing attack. For this reason, cybersecurity training is an essential component of any cybersecurity program. Even the best technical controls on a firm’s systems can be rapidly undermined by employees who are inattentive to cybersecurity risks.
In addition, the NIST Framework identifies training as a critical piece of an organization’s cybersecurity infrastructure. NIST recommends that all users (from vendors to senior executives) are informed and trained, and users understand their specific roles and responsibilities. This includes educating those users on the risks associated with the data they may encounter. Training is also a key component in the SANS Top 20. SANS recommends that organizations perform an analysis to determine where the skill gaps and points of risk exposure exist, and develop and deliver training in those areas.
Taking into account best practices from government agencies and our own internal experience, Apex Technology Services has developed training courses for managers and employees alike to ensure they are up to date with today’s latest threats and are able to conduct business in as safe a manner as possible
Apex takes training a step further by spot testing your employees to ensure they comply with the best practices presented in training sessions.
Auditing & Documentation
Apex Technology Services will pinpoint vulnerabilities in your infrastructure, process flow and internal security to ensure you are securing your data behind layers of security.
Once the vulnerabilities are identified and secured, we document the exact steps to be taken to mitigate any potential downtime.
Penetration testing
A penetration test can help determine whether a system is vulnerable to attack, if the defenses were sufficient, and which defenses (if any) the test defeated.
Penetration tests are valuable because they:
- Determine feasibility of a variety of attack vectors
- Identify high-risk vulnerabilities from a combination of lower-risk vulnerabilities
- Identify vulnerabilities that may be difficult or impossible to manually detect
- Assess the magnitude of potential business and operational impacts of successful attacks
- Test the ability of IT to detect and respond to attacks
Apex Technology Services not only has the experience to lock down your network but also to penetrate it exposing potential vulnerabilities. The best case scenario is to determine such perimeter and other weaknesses in a non-malicious fashion.
Network forensics
Network forensics is a sub-branch of digital forensics relating to the monitoring and analysis of computer network traffic for the purposes of information gathering, legal evidence, or intrusion detection. Unlike other areas of digital forensics, network investigations deal with volatile and dynamic information. Network traffic is transmitted and then lost, so network forensics is often a pro-active investigation.
Network forensics involves monitoring a network for anomalous traffic and identifying intrusions. An attacker might be able to erase all log files on a compromised host; network-based evidence might therefore be the only evidence available for forensic analysis.
Our Network forensics program can in real-time, report of suspicious network activity or traffic. It’s the proactive approach that makes the difference.
Ranked Top 10 Network security Solution Provider
One Stop Shop For All Your Technology Needs
Contact us Now!