complete infographic located at bottom
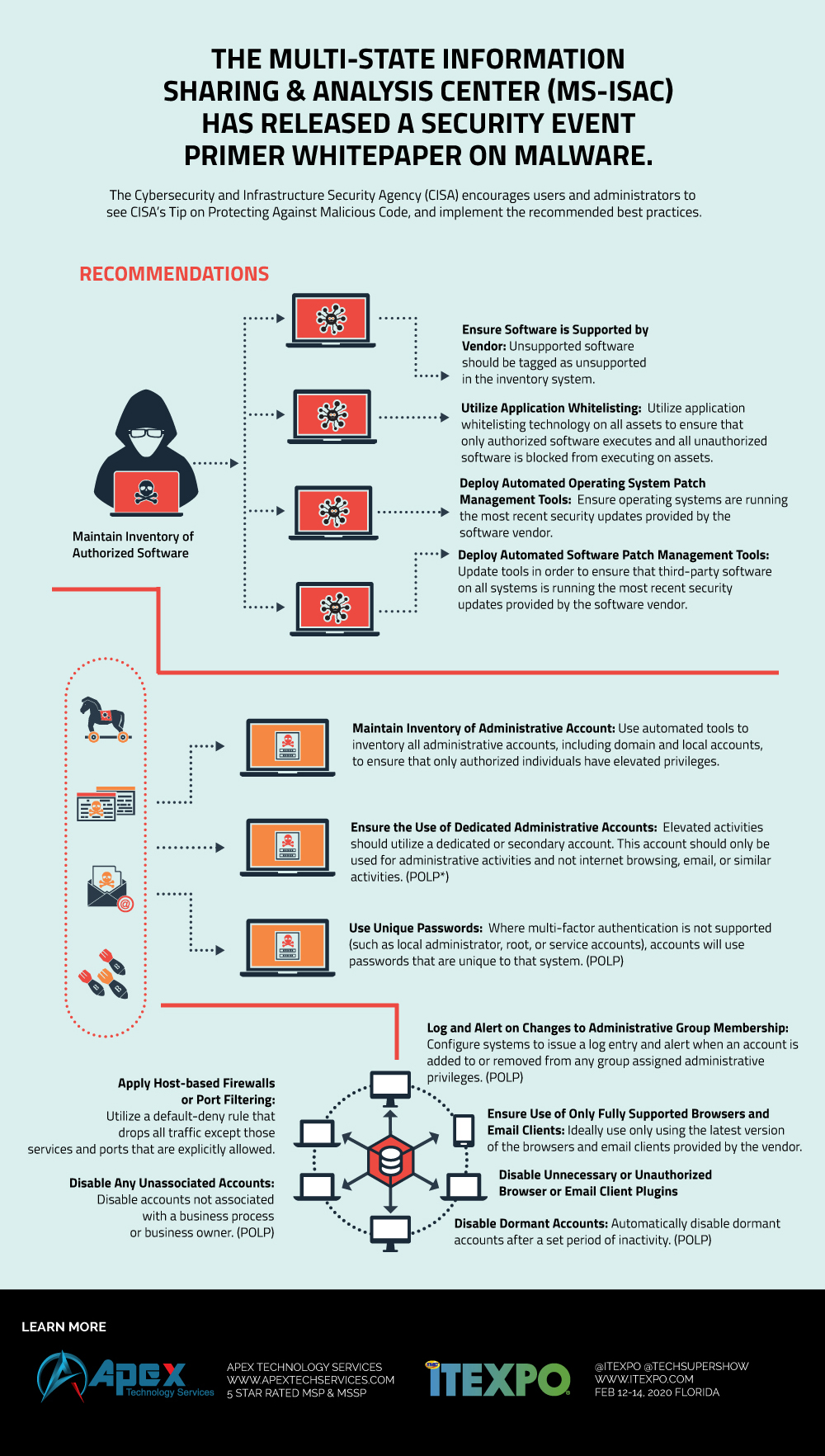
The Multi-State Information Sharing & Analysis Center (MS-ISAC) has released a Security Event Primer on Malware. The white paper outlines general malware operations and includes common malware event types and best practice recommendations. An attacker can use malware to gain access to a network, obtain sensitive data, and damage systems.
The Cybersecurity and Infrastructure Security Agency (CISA) encourages users and administrators to review MS-ISAC’s White Paper: Security Event Primer – Malware, see CISA’s Tip on Protecting Against Malicious Code, and implement the recommended best practices.
Here are the main points to be aware of:
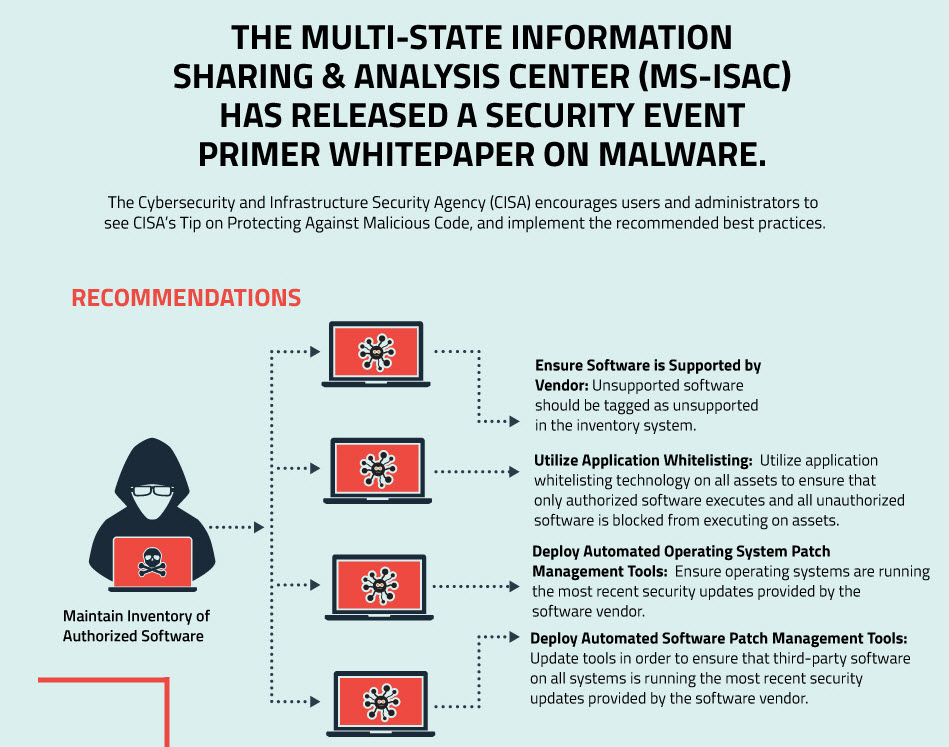
- Maintain Inventory of Authorized Software
- Ensure Software is Supported by Vendor: Unsupported software should be tagged as unsupported in the inventory system.
- Utilize Application Whitelisting: Utilize application whitelisting technology on all assets to ensure that only authorized software executes and all unauthorized software is blocked from executing on assets.
- Deploy Automated Operating System Patch Management Tools: Ensure operating systems are running the most recent security updates provided by the software vendor.
- Deploy Automated Software Patch Management Tools: Update tools in order to ensure that third-party software on all systems is running the most recent security updates provided by the software vendor.
- Maintain Inventory of Administrative Account: Use automated tools to inventory all administrative accounts, including domain and local accounts, to ensure that only authorized individuals have elevated privileges.
- Ensure the Use of Dedicated Administrative Accounts: Elevated activities should utilize a dedicated or secondary account. This account should only be used for administrative activities and not internet browsing, email, or similar activities. (POLP*)
- Use Unique Passwords: Where multi-factor authentication is not supported (such as local administrator, root, or service accounts), accounts will use passwords that are unique to that system. (POLP)
- Log and Alert on Changes to Administrative Group Membership: Configure systems to issue a log entry and alert when an account is added to or removed from any group assigned administrative privileges. (POLP)
- Ensure Use of Only Fully Supported Browsers and Email Clients: Ideally use only using the latest version of the browsers and email clients provided by the vendor.
- Disable Unnecessary or Unauthorized Browser or Email Client Plugins
- Apply Host-based Firewalls or Port Filtering: Utilize a default-deny rule that drops all traffic except those services and ports that are explicitly allowed.
- Disable Any Unassociated Accounts - Disable accounts not associated with a business process or business owner. (POLP)
- Disable Dormant Accounts Automatically disable dormant accounts after a set period of inactivity. (POLP)
POLP stands for policy of least privilege and is an important concept. There are a few areas where this can be very important. In the first instance, a user is given more privileges than they need to do their jobs. For example they are given admin rights. Even if the person does not act maliciously, it is conceivable that they get hacked and their privileged access allows other computers on the network to be affected.
We have seen ransomware spread quickly in an organizatiuon as a result of POLP not being adhered to.
Also - when a person changes roles. For example from accounting to marketing... They no longer need accounting access or privileges.
We suggest all organizations do the following to stay secure:
- Read cybersecurity essentials – a simple list which will help most organizations become far more secure.
- Go to a phishing simulation vendor and sign up for one of their offerings. Phishing Box, KnowBe4 and Phish360; are all great. This is needed to train workers by testing them without their knowledge by sending real-looking emails to their inboxes. If they click, they are immediately trained on what not to do.
- We also recommend you get a free evaluation of your cybersecurity risk from an MSP/MSSP immediately – they can also help you build in the needed compliance to reduce the risk of being fined.