Ransomware is one of the most effective strategies to illegally earn money on the internet.
Nations such as North Korea, terrorists such as ISIS and even hacker entrepreneurs or hacktrepreneurs have gotten into the act to earn easy money.
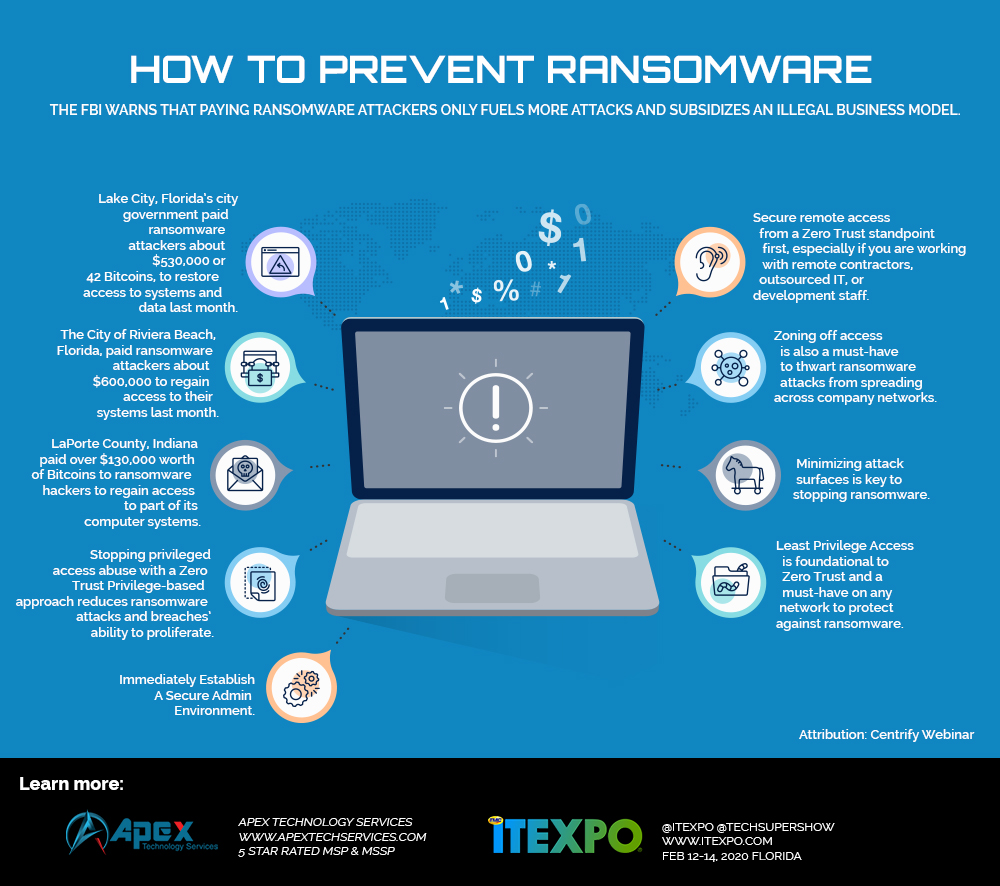
A ransomware infection basically takes every file on a computer network and scrambles it so it is unreadable or even unfindable.
If not stopped, every machine on a computer network becomes unusable.
Typically, a ransom message is flashed on a screen requesting payment to unlock files.
Hackers have set up call centers to assist you in paying – generally done via bitcoin which is tougher to track than typical transactions.
This has proven to be a highly effective strategy and cities and states are being specifically targeted and dozens have been affected.
In extreme cases – hackers wipe all information permanently. NotPetya was such an attack and it caused more than $10 billion in damage.
Infections are spread via the following methods:
- Unpatched systems can be scanned for and infections can be inserted on a machine as a result.
- Phishing – blanket emails are sent out which appear to be from a reputable source. Once a link is clicked, the malware is installed and starts locking up computers.
- Spear-Phishing is a targeted variant of phishing and it specifically targets a user based on information which is found about them. For example if a user has posted they like country music, they may be sent a country music related offer which causes them to click.
Various types of ransomware are Cryptolocker, CryptoWall, TorrentLocker, WannaCry, Petya, SamSam and Bad Rabbit.
Once infected, there are a few options:
A user can pay the ransom and hope files are unlocked. This can cost thousands or hundreds of thousands of dollars. Once again, there is no guarantee files will be unlocked and it is possible for hackers to leave a back door on the system, allowing them to re-infect systems at a later date. This is generally recommended as an option if a company is desperate. If this choice is made – it is strongly advised that systems get wiped and reinstalled.
A user can wipe systems, reinstall operating systems and then restore from backups – which hopefully exist. Ideally, a backup appliance which has a cloud option is available to restore from. Restoring large amounts of data from the cloud alone, could take days or weeks.
How can ransomware be prevented?
While there is no foolproof method to stop these attacks, it is essential to patch systems and also train users. Also:
- Read cybersecurity essentials – a simple list which will help most organizations become far more secure.
- Go to a phishing simulation vendor and sign up for one of their offerings. Phishing Box, KnowBe4 and Phish360; are all great. This is needed to train workers by testing them without their knowledge by sending real-looking emails to their inboxes. If they click, they are immediately trained on what not to do.
- We also recommend you get a free evaluation of your cybersecurity risk from an MSP/MSSP immediately – they can also help you build in the needed compliance to reduce the risk of being fined.



